|
That's right! All someone needs is a one-minute sampling of your voice to clone it! Using artifical intelligence, this company can clone your "voice DNA" to not only generate sentences with your voice, but with human emotions like anger, stress or sympathy. So powerful, it can generate 1,000 real-time sentences in less than a half a second. Of course, there are ethical concerns despite the practical uses such as virtual assistants, audio book reading with celebrity voices, speech synthesis for the disabled and for voice-overs for movies and video games. Get the scoop here.
#news #security
0 Comments
Developed by The Tor Project in 2002, and based on Firefox’s browser, the Tor Browser was built for users to access the internet anonymously via the Tor network. Your activity and identity are masked by Tor, which encrypts your traffic in at least three layers by “bouncing your communications around a distributed network of relays” selected from thousands of volunteer computers.
Tor (originally called The Onion Router because it layers your traffic like an onion) is a free network of servers, or ‘nodes’, that randomly route internet traffic between each other in order to obfuscate the origin of the data. The Tor Browser can significantly increase a user’s privacy and anonymity online. In internal documents, the NSA even refers to Tor as “the king of high-secure, low latency internet anonymity.” Tor does not replace your VPN, as it only anonymizes your browsing and a few other select services (which need to be specifically configured). Connecting to Tor through VPN connection is a great way to maintain your internet privacy and security. Not only will it hide your browsing data from your VPN company, it will also hide your home IP address from the Tor entry node. Find out more about the Tor Browser here. As always, The GoTo Tech Guru is here to help with your security issues & concerns! #security Sometimes a file is just too large to email either due to excessive upload/download time or ISP limits. When this happens, the alternative is to send a link to the file. But you don't want that link sitting out there forever nor for people to have unlimited download ability. You also want security. Introducing Mozilla Send. This cross-browser web app allows you to send self-destructing files (via a link) up to 1GB for free! The link will only work for 24 hours or for a certain number of downloads, whichever comes first. But that's not all it offers! Check it out here!
#security Every time you run a search online, the websites where you maintain an account can record that information. This data—collected and stored by search engines like Google, social media networks like Facebook, and retail giants like Amazon — won't disappear when you erase your browser's search history. Here's how to purge your search history on some of the biggest and most popular search engines, social media networks, and retail websites.
#security #google Logging in with Facebook, the social network's universal login API, allows users to carry their profile information to other apps and websites. You've probably used it to log in to services like Spotify, Airbnb, and Tinder. But sometimes, especially on lesser known websites, using Facebook's universal login feature may carry security risks. Find out what to do here!
#security
Passwords are your first line of defense against hackers and snoops trying to break into your accounts. You want your passwords to be rock solid so hackers don't even have a hope of breaking them, but that often isn't the case. Here are the most common password mistakes people make, so you know what not to do.
#security Dog is man’s best friend, but a Device Detection Dog is a cybercriminal’s worst enemy. If you’re stashing illegal data of any kind, a well-trained K-9 will find it. You can flush it, bury it, put it in your gas tank, swallow it, but you can’t hide electronic evidence from a detection dog. But data doesn't have a scent that a K-9 can smell right? So how does a dog find it? Well, read here to find out!
#security Part of the popularity of Windows may be that its super helpful in every day life, like alerting you to head to the airport 30 minutes earlier because traffic is heavy. And how does it know? Windows 10 accesses your calendar, emails and location, combines it with online traffic news and there you have it! There's a lot of private info you're giving up, and not everyone is comfortable with that, so what can you do about it? Read this article and find out how to protect yourself!
#windows #security We all like to think we could spot a scam from a mile away, but sneaky criminals are constantly improving their techniques and coming up with clever ways to extract financial and personal information. So how good are you at sniffing out at scam?
Here’s a quick test that can tell you. #security Your posts can be evidence. Anything you post or write through the site could be used against you in a court of law. While privacy settings may limit who can view your posts in a general sense, when the law gets involved, you might have to share more than you want. Find out here how this came to be and what's involved.
#security One of the most popular new trends hackers are using is to steal access to a user's webcam and spy on the user for potentially ransom-worthy footage. If the camera on your computer has been compromised, hackers may have an open window into your life and you may never know. So how do you know if hackers have infiltrated your device and what can you do about it? Find out here!
#windows #mac #security As most know, VPN offers the benefit of securing your internet traffic. This is accomplished when your data goes through a secure connection. That means yes, you are using data when you use one. If you are on a plan that has a data cap, you will use an additional amount with a VPN, more than without a VPN. Find out why this is and how it works here. As always, The GoTo Tech Guru is here to help with any questions or the implementation of VPN on your computers.
#security Whether you are being censored by your government or a private or public organization, you know that online censorship is more common than people think. Connecting to a VPN is easy to do and will solve the problem most of the time. However, you may have experienced some situations that stop that process. Those include blockades by governments, schools, colleges, and even many private companies. If you are not in the targeted area to view some content, you will be blocked because of geo-restrictions.
This guide will help you bypass VPN restrictions. As always, The GoTo Tech Guru is here to help with any questions or the implementation of VPN on your computers. #security A Virtual Private Network (VPN) redirects your connection to the Internet via a remote server run by a VPN provider. This way, the VPN server becomes a secure launching pad for you before you access various websites. All the network traffic between your device and the VPN server is directed through a secure virtual tunnel. All of the data sent and received is encrypted. Best of all, your device appears to have the IP address of the VPN server, protecting your true identity. As far as websites are concerned, you’re browsing from the server’s geographical location, not your computer’s location.
There are two types of VPN, which are different and can make a difference depending on your goal. This article will explain the differences and how best to leverage them. As always, The GoTo Tech Guru is here to help with any questions or the implementation of VPN on your computers. #security The appeal of escaping Google comes down to privacy. Google collects an alarming amount of data about you. To understand how Google does this, how it affects you, and how to delete your data from Google to protect yourself and be off-the-grid, see this article.
#security #google Check out these 10 handy, fun and downright helpful ways to use USB thumb drives.
#techgadgets #mac #windows #security #software Google provides users with several other security options, some of which you may have never heard of. Find out here!
#google #security Like most things with technology, it's not a simple yes or no answer. "It all depends on the make and model of the device. If you're able to get into the phone, there's always a chance for you to recover deleted text messages. Getting the texts you want, that's up in the air. If you're looking to recover deleted data, we're at the mercy of what's left on the device." says Trent Leavitt, manager of computer forensics at Decipher Forensics. Read here to find all the in's & out's.
#iphoneipad #android #security With the average person spending anywhere between 20 to 27 hours on the Internet every week, it is natural to wonder which of the biggest web browsers give us the best online security and privacy. Well, fret not, because that’s exactly what we’re all here to find out.
#security #google Fears about the privacy of our data have become commonplace amid credit monitoring hacks and a political firm accessing Facebook users' information. A recent arrest takes it one step further, raising questions about how our genetic information is being used and who has access to it.
The arrest was made on the basis of genetic information using an open-source genetic database, GEDmatch, to explore family trees. Anyone can use GEDMatch, a website for amateur and professional researchers and genealogists. The site's free tools allow people to enter their DNA profiles or genealogical data -- the information received from commercial genetic testing companies such as 23andMe or Ancestry.com -- so they can find familial matches with other users. In short, the investigators tracked down DeAngelo based on genetic information provided not by him but by one of his relatives. To find out how this was done and if your DNA can be used against you or any relatives, read here! #security Google was embarrassed when its algorithms incorrectly labeled a black couple as “gorillas.” Unable to stop its image-recognition algorithms working in this way, Google recently “fixed” its them by removing “gorilla” as a classification altogether. The maker of smart GIF search engine Gfycat recently took on this similar problem — and by training its image recognition on non-white faces, it has been able to develop facial-recognition software that is far better than its rivals at recognizing non-white individuals. Find out the latest about this tech here!
#news #security The FBI has been unable to retrieve data from more than half of the devices it’s tried to access. The Bureau was unable to access the contents of about 6,900 devices in the first 11 months of the fiscal year. Get the scoop here!
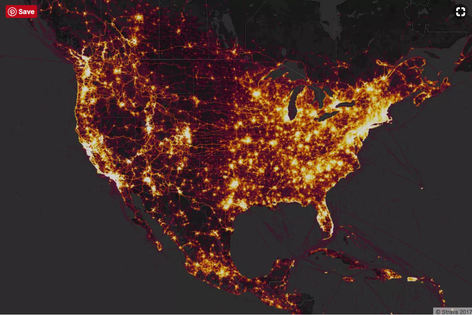
#news #security Strava is the maker of a fitness-tracking app that uses a phone’s GPS to track when and where a user is exercising. Last November, the site released a heat map showing the activity of its users from around the world, containing information across 3 trillion latitude and longitude points. The result is a pretty image of people working out, but one analyst points out that the map makes it very easy for someone to figure out the locations of military bases and the routines of their personnel. Read here how this determination was made!
#security #techgadgets Surveillance in China means the authorities know pretty much everything about you whenever you appear on camera. Now police there have a new weapon with which to fight crime and capture criminals: high-tech glasses that allow for facial recognition at the push of a button. Here's what's behind the tech!
#news #techgadets #security If you already love Gmail, you're probably going to like it more soon. Google is coming out with a massive update for Gmail in the coming weeks and it's going to have some cool new features. Among several other cool features like password protecting emails, there will be a self-destruct option for emails! Yep! To get the inside scoop, read here!
#google #security |
Blog AuthorI love technology and how it enhances our lives! Just think, without the Apollo moon missions, we might not have calculators! Imagine!! Archives
October 2018
Categories
All
|




















 RSS Feed
RSS Feed